Thursday, September 22, 2005
Security SNR (Signal Noise Ratio)
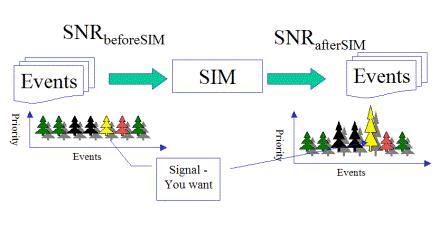 At the security information management area, the concept of SNR is often used to describe the performance of a SIM tool. But, what’s SNR? what impact the security SNR output? I hope this diagram help.
At the security information management area, the concept of SNR is often used to describe the performance of a SIM tool. But, what’s SNR? what impact the security SNR output? I hope this diagram help.
Wednesday, September 21, 2005
Mini-Microsoft
Tuesday, September 20, 2005
Ajax is a famous football club?
Ajax is not the name of the famous football club at Netherland. It's a series of technologies which incorporates:
# Standards-based presentation using XHTML and CSS;
# Dynamic display and interaction using the DOM;
# Data interchange and manipulation using XML and XSLT;
# Asynchronous data retrieval using XMLHttpRequest;
# and JavaScript binding everything together.
Friday, September 16, 2005
Tapping the Matrix, Part 1
Tapping into the Matrix, Part 1 by Carlos Justiniano -- In this first article of a two-part series on harnessing the idle processing power of distributed machines, Carlos Justiniano explains the current trends in this exciting technology area, then drills down into specifics such as client/server communication, protocols, server design, databases, and testing.
What's P2P?
There are many definitions to peer to peer technology. The following is some characteristics of P2P:
Everything except the client/server model
可以认为除了C/S架构之外的所有东西都是P2P架构的,实际上C/S才是特殊的,而P2P则是普遍的。
Network of nodes with equivalent capabilities/responsibilities (symmetrical)
P2P网络中的节点具有对等的能力和责任,是对称的。
Nodes are both Servers and clients called “Servents”
P2P网络中的节点同时即是服务器,也是客户端。
Thursday, September 15, 2005
Security Management, OR Infrastracture Management
所以,对网络中的IP分组数据除了保证其可达性、延时、安全性等之外,对其有效的监视、分类和控制是运营商能够立足于3G/NGN年代的基础能力。
Security management is having a much wide meaning to those telecommunication carriers, bandwidth mangement, performance management, traffic shaping, identity and accounting.... I am fraid that you can not find out what's not security related.
Wednesday, September 14, 2005
"Proprietary" crypto of Skype
At the message of VOIPsa mailing list, Robert Moskowitz said:
"Some time ago, on the user forum I and another pushed for information on the skype crypto and beyond 'AES 256', we were told that information is proprietary.
Sorry, I cannot accept proprietary cyrpto. I can understand 'patent pending' or such. But not silence. "
I agree. If Skype insist on its "proprietary" crypto, those enterprises and professional users, i am afraid, will hesitate to adopt it as their primary communication tools.
Tuesday, September 13, 2005
P2P and Instant Message
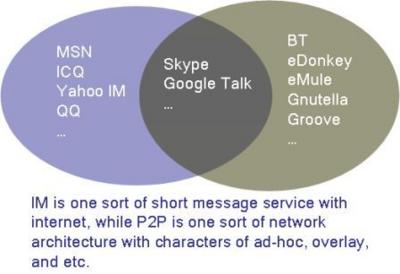 IM(Instant Message) and P2P(Peer to Peer) are two of the most popular terms at Internet. This diagram depicts the relationship between them with examples. What they are bring to end users, software vendors and the internet service providers? business opportunities, security threats. what's your opinion?
Enjoy.
IM(Instant Message) and P2P(Peer to Peer) are two of the most popular terms at Internet. This diagram depicts the relationship between them with examples. What they are bring to end users, software vendors and the internet service providers? business opportunities, security threats. what's your opinion?
Enjoy.
eBay bought Skype with 2.4B$
Oracle Agrees to buy Siebel
Monday, September 12, 2005
Skype Protocol Reverse-Engineering
Do you believe that a researcher from China claimed that he has broken into the protocol used by Skype, ie. he can open skypenet without the skype client. In fact, a mini-skype is under developing with his own code.
http://publishblog.blogchina.com/blog/tb.b?diaryID=1546484
Might you want to skype him at: callto://shreksz/
Google与微软eBay等全面开战 到底想干什么
An interesting blog entry at:
http://blog.sina.com.cn/u/3fe543b00100001n
Just as what I comment a few days ago: while Microsoft dorminate the desktop operating systems, Google will dorminate the desktop information.
M2M-X by NTT
I run into a document by NTT, which described a platform based on P2P and IPv6.
M2M-X means "Machine to Machine for any[thing|place|time]", where the "m2m-x Management Server" functions as:
- Authentication
- Access control
- Issuance/distribution of encryption keys
- Visible only for authorized peers
- Firewall control
Oops, do you have any comments on it?

